Transform your talent attraction with employee voices
The AI-enabled employee-generated content platform to bring your employee experience to life
to see how you can 2.5x your engagement with guaranteed results from month one











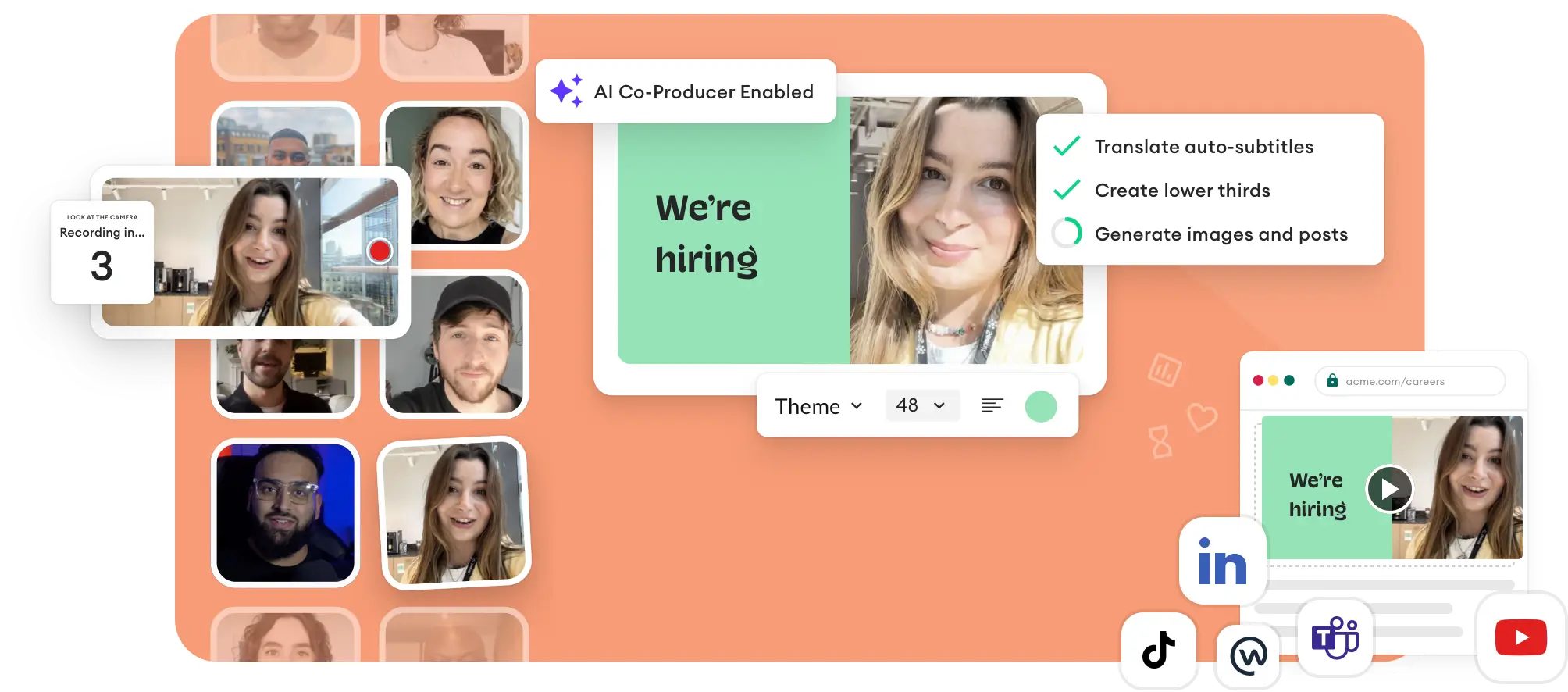




















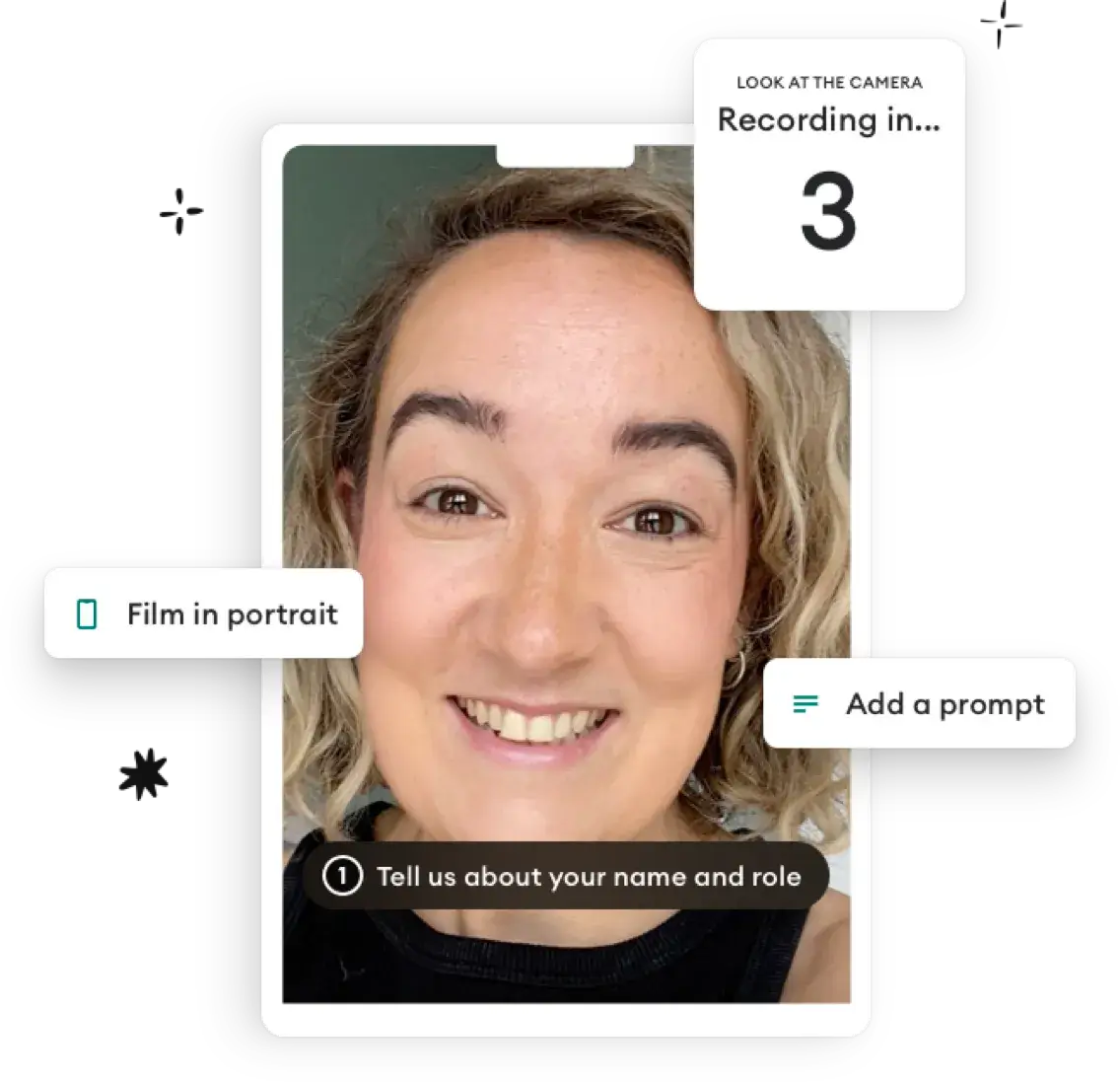
 Collect
Collect
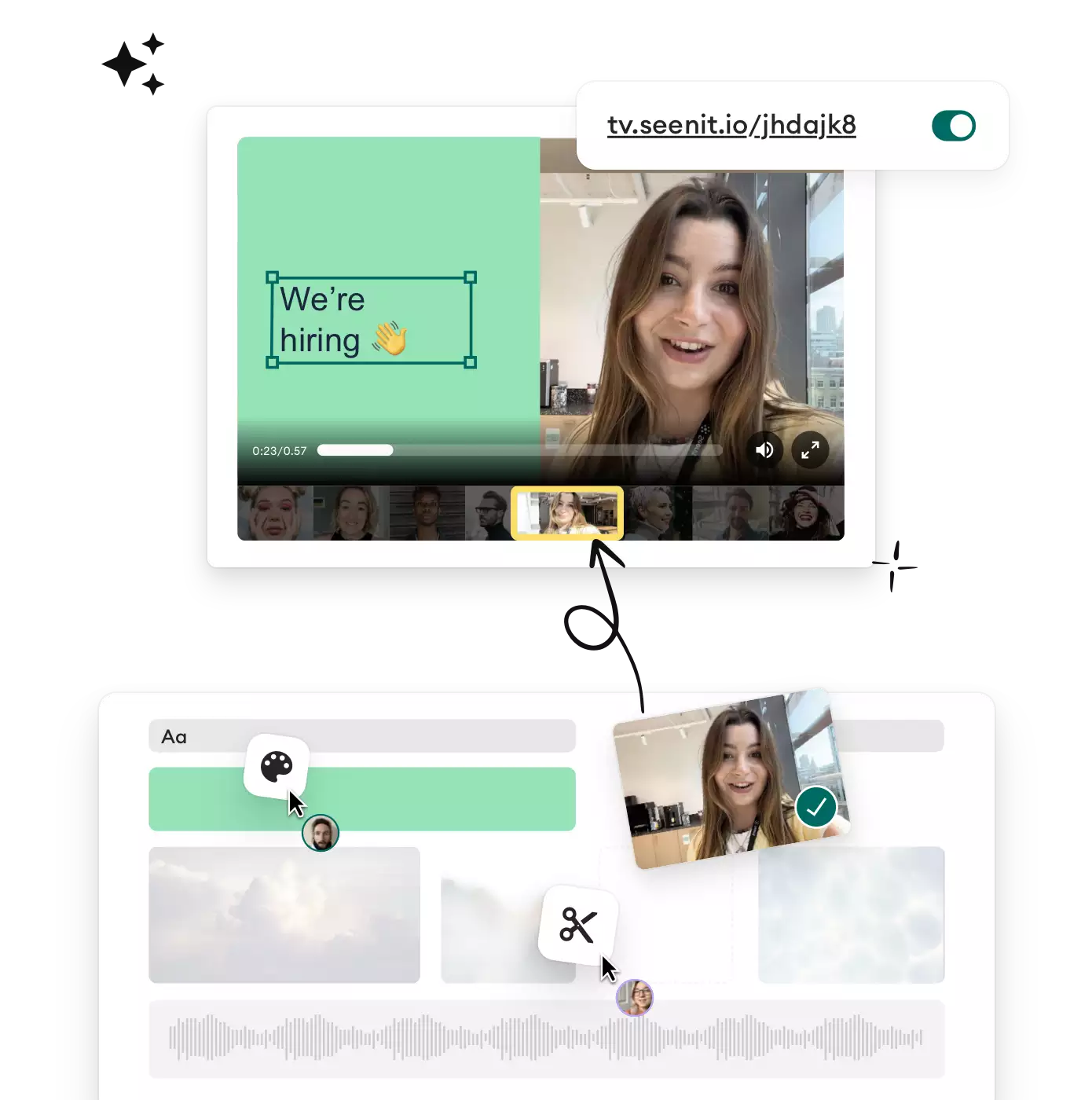
 Edit & Host
Edit & Host
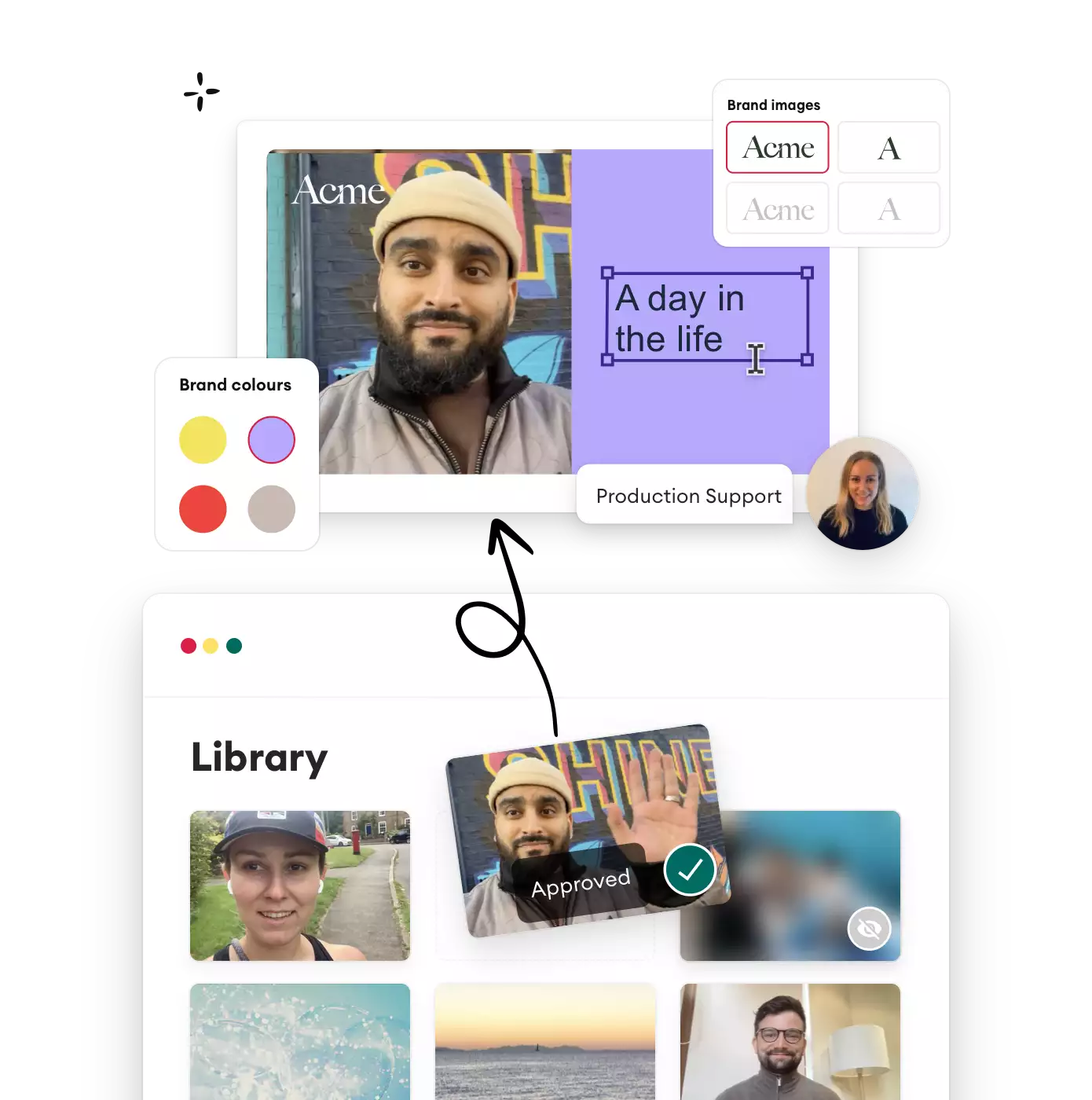
 Manage & Scale
Manage & Scale